Application Security is a Core Tenet of Zero Trust
Zero trust requires all users to be authenticated, authorized and continuously validated for security posture before accessing applications and data. As organizations make progress in their zero trust journeys, leaders are focusing on the next challenge: software application security. These leaders dive into the strategy, testing and evaluation, advances in analytics and more that are bolstering security features within applications to prevent vulnerabilities against evolving threats.

-
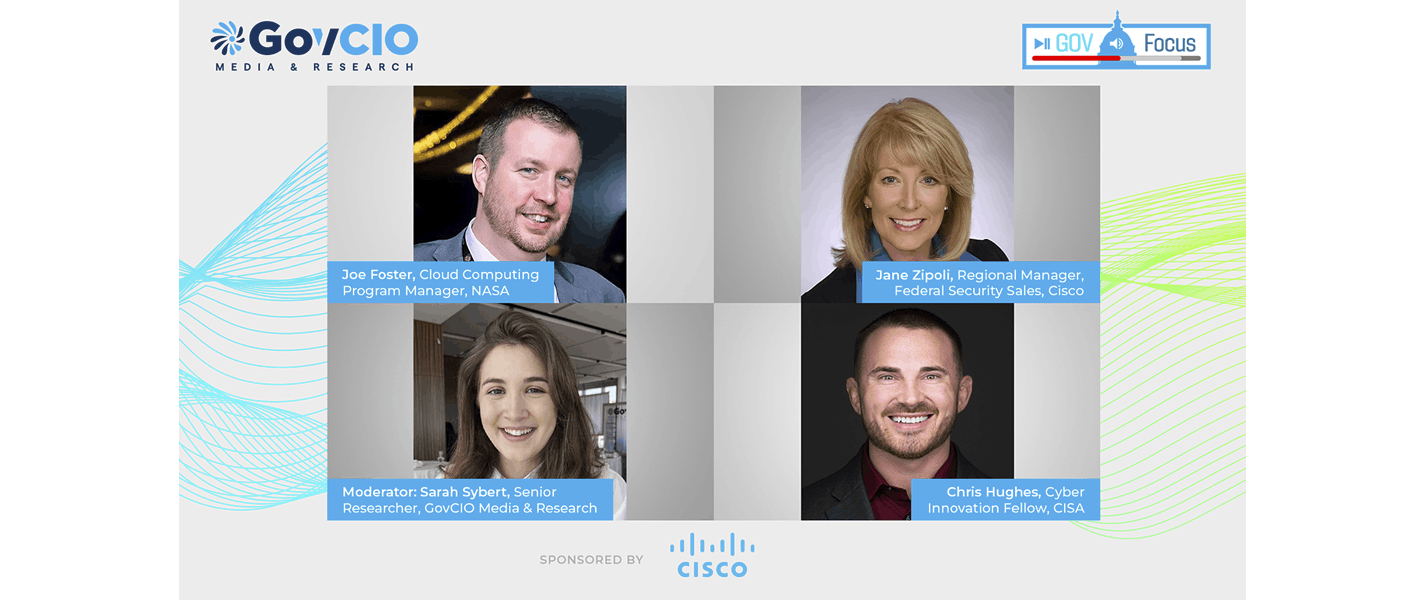
 Joe Foster Cloud Computing Program Manager, NASA
Joe Foster Cloud Computing Program Manager, NASA -
 Chris Hughes Cyber Innovation Fellow, CISA & Co-Founder and CISO, Aquia
Chris Hughes Cyber Innovation Fellow, CISA & Co-Founder and CISO, Aquia -
 Jane Zipoli Regional Manager, Federal Security Sales, Cisco
Jane Zipoli Regional Manager, Federal Security Sales, Cisco
-

Q&A: DOGE Caucus Tackles Government Inefficiency with Tech
House DOGE Caucus Co-Chair Rep. Pete Sessions discusses budgeting, updating outdated systems and ensuring data integrity.
5m read -

HIMSS: Unlocking Interoperability to Make Health Data Work for Everyone
The Sequoia Project's CEO shares how she's thinking about the role of data standards development toward EHR interoperability.
8m watch -

NIST's Latest Guidance Bolsters Identity Management
NIST is advancing zero trust and identity management with new guidance on cybersecurity, authentication and digital identity.
5m read -

Defense Officials Talk Commercial-First Approach to CJADC2
Industry will play a large role in piloting and scaling solutions within the combined information and decision advantage approach in CJADC2.
4m read












