Public-Private Partnerships May Revolutionize Airport Security
TSA is looking to move beyond traditional security screening methods to increase efficiency and decrease wait times.
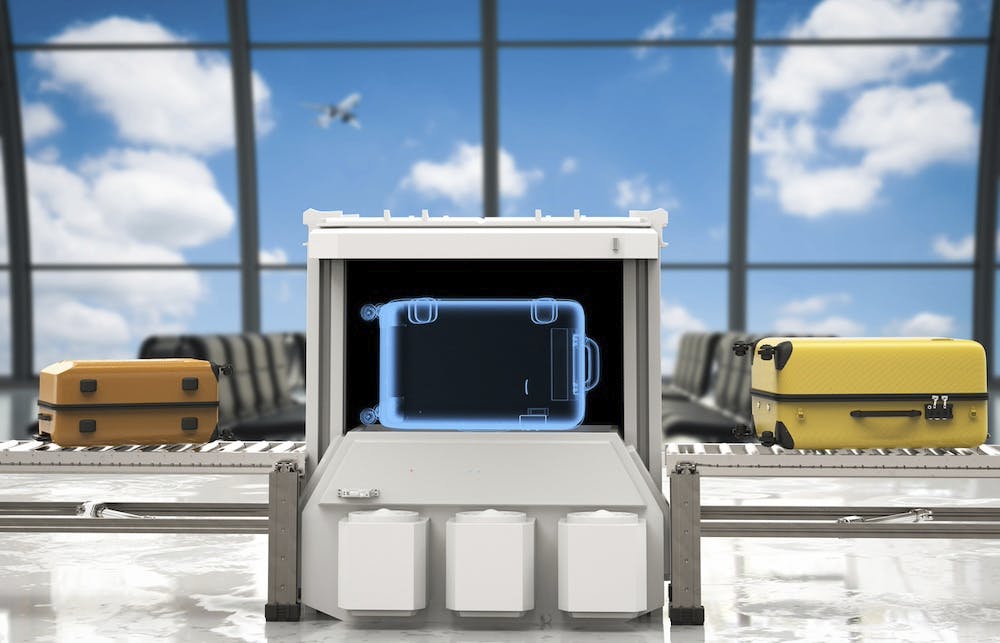
Computed tomography scanners, which have been used for years in scanning checked luggage at airports, are now being piloted at airport checkpoints for carry-on bags. The broader application of the technology could someday afford all travelers the perks currently granted to those in the Department of Homeland Security’s Trusted Traveler Programs such as Global Entry and PreCheck.
By employing CT scanners at TSA checkpoints, airline passengers could begin leaving their liquids and laptops in carry-on luggage and their jackets on as they pass through security, which would reduce the security experience but not the security.
This would help curb one of the agency’s greatest challenges as “people want to feel secure without feeling security,” said Transportation Security Administration Executive Assistant Administrator for Security Operations Darby LaJoye at the July 31 DHS Centers of Excellence Summit in Washington, D.C.
TSA is also interested in eliminating the use of government identification cards or boarding passes to verify passenger identity. In conversations with industry, it is exploring how a biomarker could relay the same information.
“Having a laminated card that tells somebody that I am who I am — that’s old,” said LaJoye. “Even the idea of a boarding pass on your phone, we’re sort of getting past that.”
Implementing credential authentication technology is one of two things TSA is doing, in addition to CT, that LaJoye considers most important. The technology will have “a direct feed back to a vetting system” to indicate the validity of a form of identification within seconds.
New technologies can only be so effective, however, in solving TSA’s challenges. There are physical limitations that prevent airport security from reaching its full potential.
“Almost 50% of the largest airports in the country, a class 1 [airports serving all types of scheduled operations of air carrier aircraft designed for at least 31 passenger seats] or category X [airports that have the largest number of passenger boardings] airports have at least one checkpoint that’s capacity constrained,” said LaJoye. “I can helicopter in 100 officers. It’s not going to help that wait time at all because there’s simply no more room to grow the checkpoint, irrespective of what kind of technology you’re putting out there.”
Public-private partnerships have been “tremendous” for TSA, as the agency can leverage the “competitive entrepreneurial spirit” of industry to reduce the footprint of technology at airports.
“Industry loves TSA because there are 440 airports, there are 2,400 lanes — every one of which have technology and computers and machines they can give to the government,” said LaJoye. “Airports want to be competitive.”
Many companies are drawing inspiration from international airports in Europe and Asia for new technologies, according to LaJoye. While there is no shortage of creative ideas in Washington, D.C., it is important that they be deployed in a manner to which the public will be receptive.
As for LaJoye’s parting words to Centers of Excellence researchers, he said, “Don’t think like a scientist …Think like a scientist and a citizen because there’s this demand for security against the right for privacy.”
This is a carousel with manually rotating slides. Use Next and Previous buttons to navigate or jump to a slide with the slide dots
-

Federal Leaders Revamp Tech Workforce, Policy
Despite the rise in interest of emerging technology, federal leaders see data, policy and the workforce as a best vehicle for change.
4m read -

Pentagon Selects Second Tranche of Replicator Drone Program
The second tranche of systems is part of the DOD’s two-year plan to field thousands of autonomous systems by August 2025.
5m read -

Looking Back at the First Trump Administration's Tech Priorities
In his first term, Donald Trump supported cybersecurity, space policy and artificial intelligence development.
4m read -

Securing the Expanding Attack Surface in Cyberspace
Agencies undergoing digital transformation face a more intricate threat landscape and a wider threat target for adversaries looking to exploit vulnerabilities. This panel dives into strategies agencies are undertaking to safeguard these complex environments, including zero-trust architecture, vigilant monitoring and robust cybersecurity training.
30m watch







