Zero Trust
-

Army Scales Up Its Bring Your Own Device Program to More Soldiers
BYOD program will let soldiers and DOD civilians securely access government systems through their personal devices.
7m read -

Zero Trust: Securing the Supply Chain
Hear from industry and government leaders at CISA, DOD and Fortinet Federal about how to integrate zero trust principles into supply chain security strategies to more effectively manage risk and vulnerabilities.
7m read -
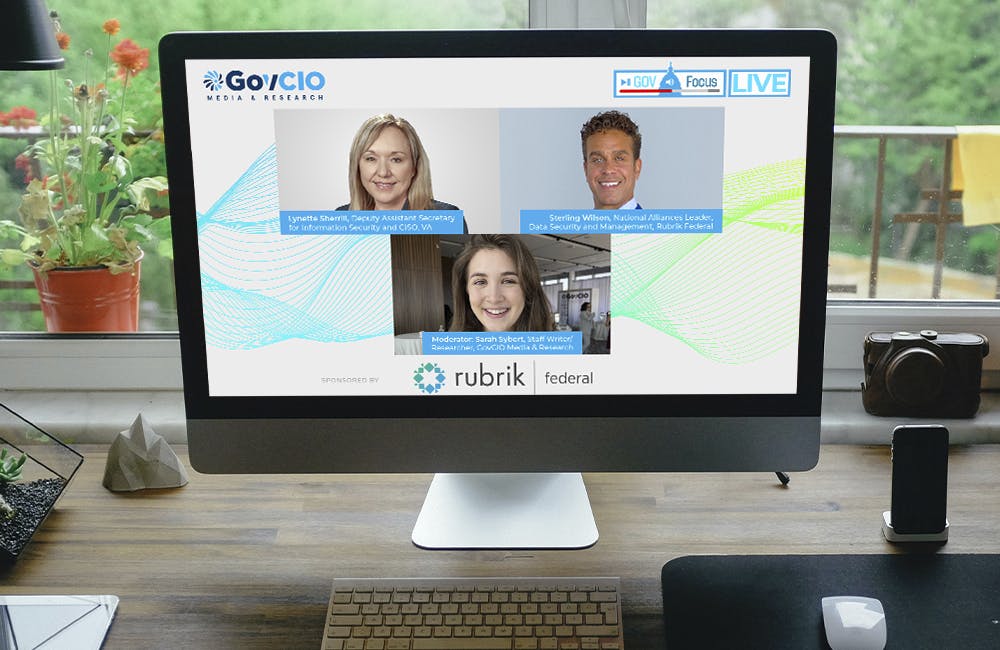
Zero Trust's Role in Securing Veteran Data
VA CISO Lynette Sherrill and National Alliances Leader of Data Security and Management at Rubrik Federal Sterling Wilson sit down to discuss how they’re preparing and advancing security frameworks to protect sensitive data.
36m watch -

AI and Automation Are Vital to Navy's Cyber Readiness
Zero trust and a strong cybersecurity culture will help the Department of the Navy prepare its data for AI.
7m read -

CISA Mandates Federal Agencies Account For Assets On Networks
CISA's new directive aims to improve asset visibility and allow to manage cybersecurity risks federal agencies face.
7m read -

Data Mapping, Operational Understanding Are Next Steps For Zero Trust
Agencies are aligning security and performance needs.
7m read -

Federal Agencies Implementing New Approaches to Software Security
Modernizing approaches to software security leads to better detecting vulnerabilities and preventing zero-day incidents like the SolarWinds attack.
7m read -

GSA Outlines Best Practices for Identity Management
Ken Myers explains how GSA’s new playbooks are guiding federal agencies’ identity management.
7m read -

Data Management Key to Successful Zero Trust Strategy, CISA Says
Data standards and governance determine federal agencies's readiness for zero trust.
7m read -

VA CIO: Zero Trust at the Core of Agency's Vision, Security-Focused Workforce
CIO Kurt DelBene stresses the importance of building the agency's vision and workforce upon the fundamental aspects of zero trust.
7m read -

Zero Trust Defines Software Supply Chain Security at CFPB, DOE
CFPB and DOE shift their attention to zero trust as they work to eliminate risks and build a higher level of protection around their software supply chains.
5m read -
Flywheel Fridays - What You Need to Know About Zero Trust
Join our hosts for an update on evolving federal cyber priorities.
16m listen














